NOTICE: Infinity N5.2 and N5 FAQ 0.0.0
The wiki has been updated to include the N5.2 changes and the v0.0.0 FAQ.
List of wiki pages updated in N5.2.
Difference between revisions of "Quantronic Combat (Hacking)"
(PDF 2.1, Hacking Characteristics) |
(PDF N5.2 update.) |
||
| (5 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
| − | {{section-combat-module}} | + | {{n5-section-combat-module}} |
| − | {{section-hacking}} | + | {{n5-section-hacking}} |
| − | In Infinity, infowar and cyberwarfare tasks, defined as Hacking, are shouldered by the | + | In Infinity, infowar and cyberwarfare tasks, defined as Hacking, are shouldered by the [[Hacker]]s, specialized Troopers who can use the different Hacking Programs which define quantronic combat. |
{{greybox-start | Getting Started with Hacking}} | {{greybox-start | Getting Started with Hacking}} | ||
| − | According to their nature, Hacking | + | {{update | PDF 5.2, October 2025}} |
| + | According to their nature, [[Hacking Program]]s {{erratahighlight}}can either be aggressive to affect enemy Troopers, defensive to protect Allied Troopers, supportive to boost Allied Troopers or affect scenery items and objectives in scenario missions{{erratahighlight-end}}. | ||
| + | {{update-end}} | ||
| + | {{original}} | ||
| + | According to their nature, [[Hacking Program]]s {{originalhighlight}}allow the Hacker to act in an aggressive or defensive manner, support other Troopers, interact with scenery, etc{{originalhighlight-end}}. | ||
| + | {{original-end}} | ||
{{greybox-end}} | {{greybox-end}} | ||
{{remember-start}} | {{remember-start}} | ||
| − | When making your Army | + | When making your [[Army List]]s in [https://infinityuniverse.com/army/infinity Infinity Army], a summary of the [[Hacking Program]]s will be included, in the same way that a summary of your Troopers’ weapons is included. |
{{remember-end}} | {{remember-end}} | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
== Upgrade Programs (UPGRADE) == | == Upgrade Programs (UPGRADE) == | ||
| + | Custom-made software tailored to the style and preference of specific infowar operatives. If available, they will be listed in the [[Unit Profile]], in round brackets next to the name of the [[Hacker]] or the [[Hacking Device | Device]]. | ||
| − | |||
== Supportware Programs == | == Supportware Programs == | ||
| + | These are programs of extended duration which are mainly designed to support [[allied]] Troopers on the battlefield by granting them bonuses to improve their combat capabilities. Likewise, they may also be designed to hinder [[enemy]] Troopers, applying negative MODs to them. | ||
| − | + | {{supportware}} | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
== Hacking Devices and Hacking Programs: Characteristics == | == Hacking Devices and Hacking Programs: Characteristics == | ||
| − | Hacking | + | [[Hacking Device]]s and [[Hacking Program]]s have the following characteristics: |
| − | + | *They act in the user's [[Hacking Area]]. | |
| − | *They act in the user's Hacking Area. | + | *They do not require [[LoF]] to act, unless the Hacking Program's own description states otherwise. |
| − | *They do not require LoF to act, unless the Hacking Program's own description states otherwise. | + | * Only Troopers in [[Model]] form may be targeted by Hacking Programs. |
| − | |||
| − | |||
| − | * Only Troopers in Model form may be targeted by Hacking Programs. | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
* They benefit, if applicable, from the target's [[Targeted]] State. | * They benefit, if applicable, from the target's [[Targeted]] State. | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | == Example of Quantronic Combat == | |
| − | |||
| − | |||
| − | == Example == | ||
{{greybox-start | Example of Quantronic Combat (Hacking)}} | {{greybox-start | Example of Quantronic Combat (Hacking)}} | ||
| − | '''Step 1:''' | + | '''Step 1:'''<br> |
| + | The Active Trooper declares a [[Move]] from point A to point B. | ||
| − | The | + | The Reactive Trooper declares a [[Carbonite]] Hacking Program [[ARO]]. |
| − | The | + | The Active Trooper declares [[Reset]] for their second Skill of the Order. They do not declare a [[BS Attack]] against the Hacker because it is clear that they lack [[LoF]] to the Hacker along their entire movement path. |
| − | + | '''Step 2:'''<br> | |
| + | The [[Face to Face Roll]]s are performed. | ||
| − | + | Active Trooper, Reset ([[WIP]] Roll, in this case there are no MODs to apply): 1 d20 with Success Value (SV) = 13. | |
| + | Reactive Trooper, Carbonite (WIP Roll, in this case there are no MODs to apply): 1 d20 with SV = 13. | ||
| − | '' | + | They both succeed, but the Reactive Trooper's 7 cancels the Active Trooper's 3. |
| − | + | {{image | name=n5/eng-hacking-example-1.jpg | style=fullborder }} | |
| − | Face to Face Roll | + | '''Step 3:'''<br> |
| + | Therefore, as the Hacker wins the Face to Face Roll, the Active Trooper must perform 2 [[Saving Roll]]s due to [[DA]] Ammunition, against PS 7. | ||
| + | Saving Roll = 13 (PS 7 + BTS 6). | ||
| − | Active | + | Due to the 14, the Active Trooper enters [[Immobilized-B State]], placing an Immobilized-B Token next to them. |
| − | + | {{image | name=n5/eng-hacking-example-2.jpg | style=fullborder }} | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
{{greybox-end}} | {{greybox-end}} | ||
| − | |||
| − | {{ | + | {{n5-section-combat-module}} |
| − | + | {{n5-section-hacking}} | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| + | [[Category: Combat Module]] | ||
| − | [[Category: | + | [[Category: N5.2 Update]] |
Latest revision as of 10:03, 21 October 2025
Possibility of Survival (PS) | Saving Roll (SR) | Wounds | Guts Roll || Ballistic Skills | BS Attack | Template Weapons and Equipment | Direct Template Weapons | Impact Template Weapons | Ranged Weapon Profile | Intuitive Attack | Speculative Attack || Close Combat | CC Attack | Melee Weapon Profile || Quantronic Combat (Hacking)
Hacker | Firewall | Hacking Area | Repeater | Deployable Repeater | Hacking Programs Chart | Hacking Device
Hacking ProgramsAssisted Fire | Carbonite | Controlled Jump | Cybermask | Enhanced Reaction | Fairy Dust | Oblivion | Spotlight | Total Control | Trinity | White Noise | Zero Pain
In Infinity, infowar and cyberwarfare tasks, defined as Hacking, are shouldered by the Hackers, specialized Troopers who can use the different Hacking Programs which define quantronic combat.
Update PDF 5.2, October 2025
According to their nature, Hacking Programs can either be aggressive to affect enemy Troopers, defensive to protect Allied Troopers, supportive to boost Allied Troopers or affect scenery items and objectives in scenario missions.
Show original text.
Original
According to their nature, Hacking Programs allow the Hacker to act in an aggressive or defensive manner, support other Troopers, interact with scenery, etc.
When making your Army Lists in Infinity Army, a summary of the Hacking Programs will be included, in the same way that a summary of your Troopers’ weapons is included.
Upgrade Programs (UPGRADE)
Custom-made software tailored to the style and preference of specific infowar operatives. If available, they will be listed in the Unit Profile, in round brackets next to the name of the Hacker or the Device.
Supportware Programs
These are programs of extended duration which are mainly designed to support allied Troopers on the battlefield by granting them bonuses to improve their combat capabilities. Likewise, they may also be designed to hinder enemy Troopers, applying negative MODs to them.
SUPPORTWARE
- A Trooper can benefit from the effects of only one Program with the Supportware Label at a time.
- Each Hacker can only sustain one active Supportware Program at a time.
- A Hacker can cancel an active Supportware Program by declaring another Program and expending the corresponding Order or ARO.
- A Supportware Program is automatically cancelled if the target of the Supportware is targeted by a new Supportware Program, or if the Hacker running the Program enters Isolated State or any Null States.
During their Active Turn, a Player that has two Troopers with EVO Hacking Devices on the table, declares Fairy Dust with one of them and chooses REMs as the Troop Type that will benefit from this Supportware.
For tactical reasons, they decide to spend the last Order on the other Trooper with an EVO Hacking Device to declare Enhanced Reaction on a REM located in the vanguard.
By designating a REM that was already benefitting from Fairy Dust, the new Supportware Program deactivates the Fairy Dust Program and the corresponding Token is removed from the table.
Hacking Devices and Hacking Programs: Characteristics
Hacking Devices and Hacking Programs have the following characteristics:
- They act in the user's Hacking Area.
- They do not require LoF to act, unless the Hacking Program's own description states otherwise.
- Only Troopers in Model form may be targeted by Hacking Programs.
- They benefit, if applicable, from the target's Targeted State.
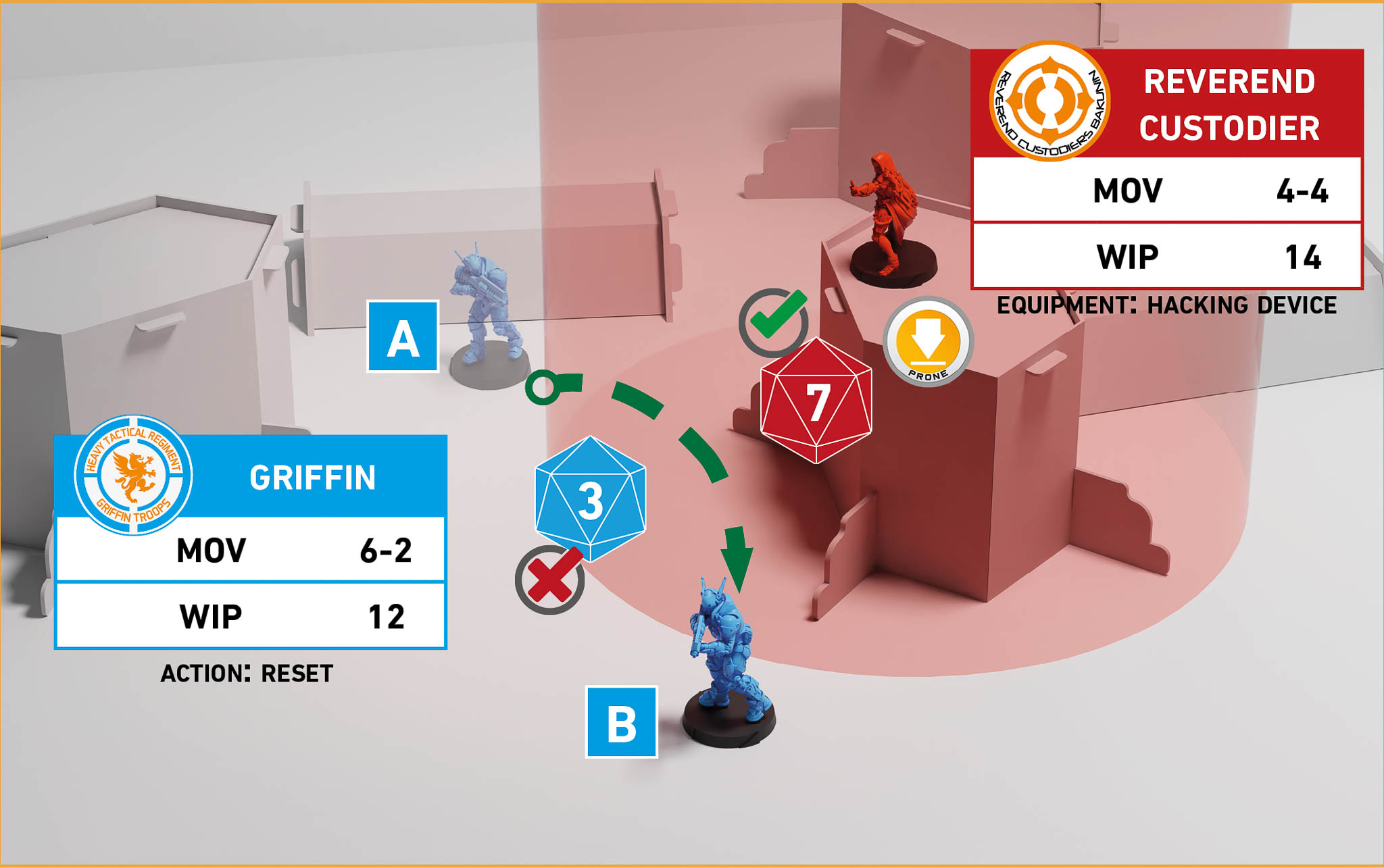
Example of Quantronic Combat
Step 1:
The Active Trooper declares a Move from point A to point B.
The Reactive Trooper declares a Carbonite Hacking Program ARO.
The Active Trooper declares Reset for their second Skill of the Order. They do not declare a BS Attack against the Hacker because it is clear that they lack LoF to the Hacker along their entire movement path.
Step 2:
The Face to Face Rolls are performed.
Active Trooper, Reset (WIP Roll, in this case there are no MODs to apply): 1 d20 with Success Value (SV) = 13.
Reactive Trooper, Carbonite (WIP Roll, in this case there are no MODs to apply): 1 d20 with SV = 13.
They both succeed, but the Reactive Trooper's 7 cancels the Active Trooper's 3.
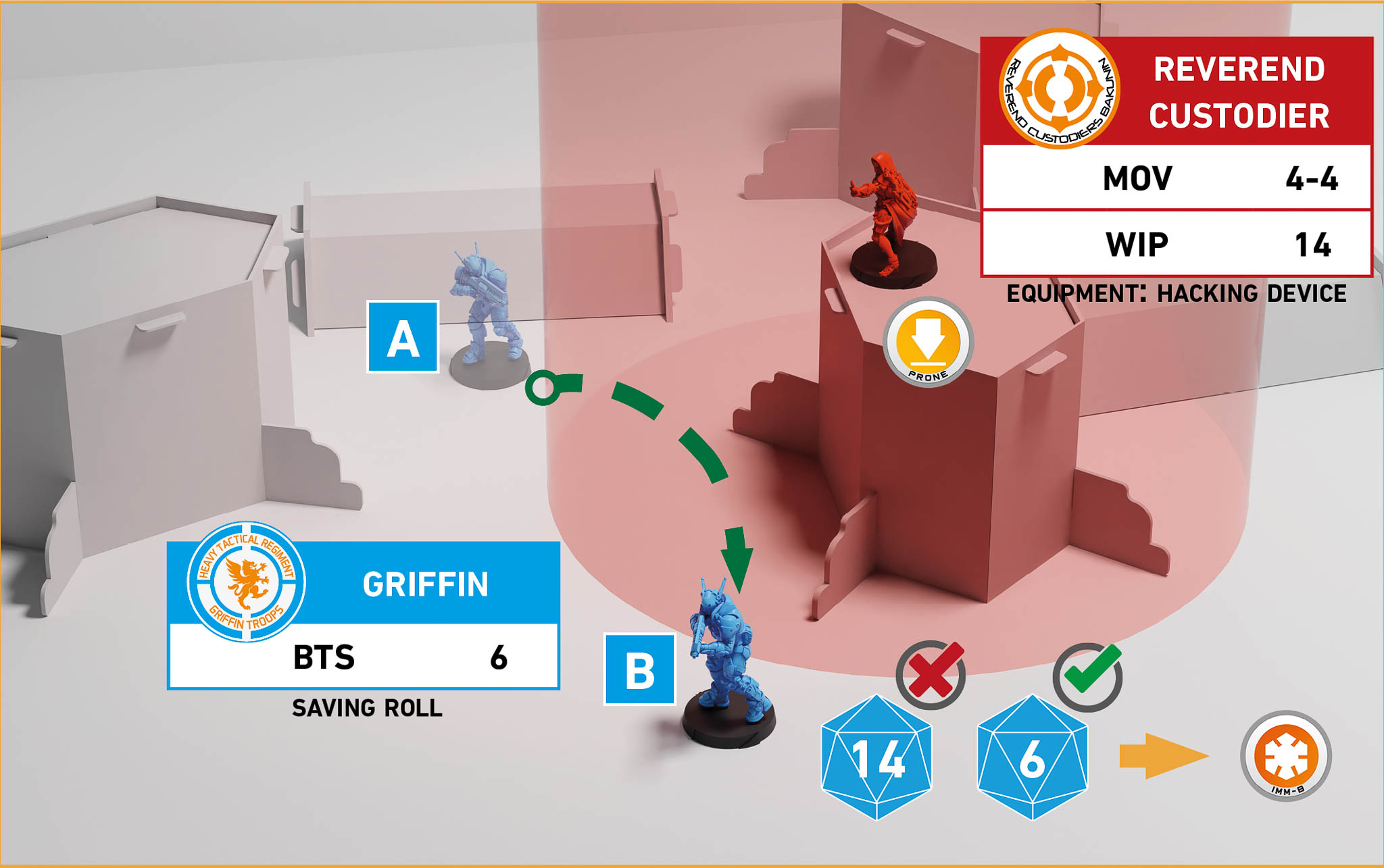
Step 3:
Therefore, as the Hacker wins the Face to Face Roll, the Active Trooper must perform 2 Saving Rolls due to DA Ammunition, against PS 7.
Saving Roll = 13 (PS 7 + BTS 6).
Due to the 14, the Active Trooper enters Immobilized-B State, placing an Immobilized-B Token next to them.
Possibility of Survival (PS) | Saving Roll (SR) | Wounds | Guts Roll || Ballistic Skills | BS Attack | Template Weapons and Equipment | Direct Template Weapons | Impact Template Weapons | Ranged Weapon Profile | Intuitive Attack | Speculative Attack || Close Combat | CC Attack | Melee Weapon Profile || Quantronic Combat (Hacking)
Hacker | Firewall | Hacking Area | Repeater | Deployable Repeater | Hacking Programs Chart | Hacking Device
Hacking ProgramsAssisted Fire | Carbonite | Controlled Jump | Cybermask | Enhanced Reaction | Fairy Dust | Oblivion | Spotlight | Total Control | Trinity | White Noise | Zero Pain