NOTICE: Infinity N5.2 and N5 FAQ 0.0.0
The wiki has been updated to include the N5.2 changes and the v0.0.0 FAQ.
List of wiki pages updated in N5.2.
Difference between revisions of "Hacking Area"
(Updated see FAQ links.) |
|||
| Line 10: | Line 10: | ||
In addition, if a Hacker is within the Zone of Control of an Enemy Repeater or Deployable Repeater, their Hacking Area includes all Enemy Hackers on the game table. | In addition, if a Hacker is within the Zone of Control of an Enemy Repeater or Deployable Repeater, their Hacking Area includes all Enemy Hackers on the game table. | ||
| − | {{seefaq}} | + | {{seefaq | Hacking Areas and AROs.}} |
Revision as of 11:47, 4 February 2021
Hacker | Firewall | Hacking Area | Repeater | Deployable Repeater | Hacking Programs Chart | Hacking Device
Programs and StatesAssisted Fire | Carbonite & Immobilized-B State | Controlled Jump | Cybermask & Impersonation State | Enhanced Reaction | Fairy Dust | Oblivion & Isolated State | Spotlight & Targeted State | Total Control & Possessed State | Trinity | White Noise | Zero Pain
This term refers to the Area of Effect of Hacking Programs. In Infinity CodeOne a Hacker's Hacking Area matches their Zone of Control.
This term refers to the Area of Effect of Hacking Programs. In Infinity N4 a Hacker’s Hacking Area matches their Zone of Control, and the Zone of Control of Repeaters and Deployable Repeaters of either the Player or their Allies.
In addition, if a Hacker is within the Zone of Control of an Enemy Repeater or Deployable Repeater, their Hacking Area includes all Enemy Hackers on the game table.
(See FAQs. Hacking Areas and AROs.)
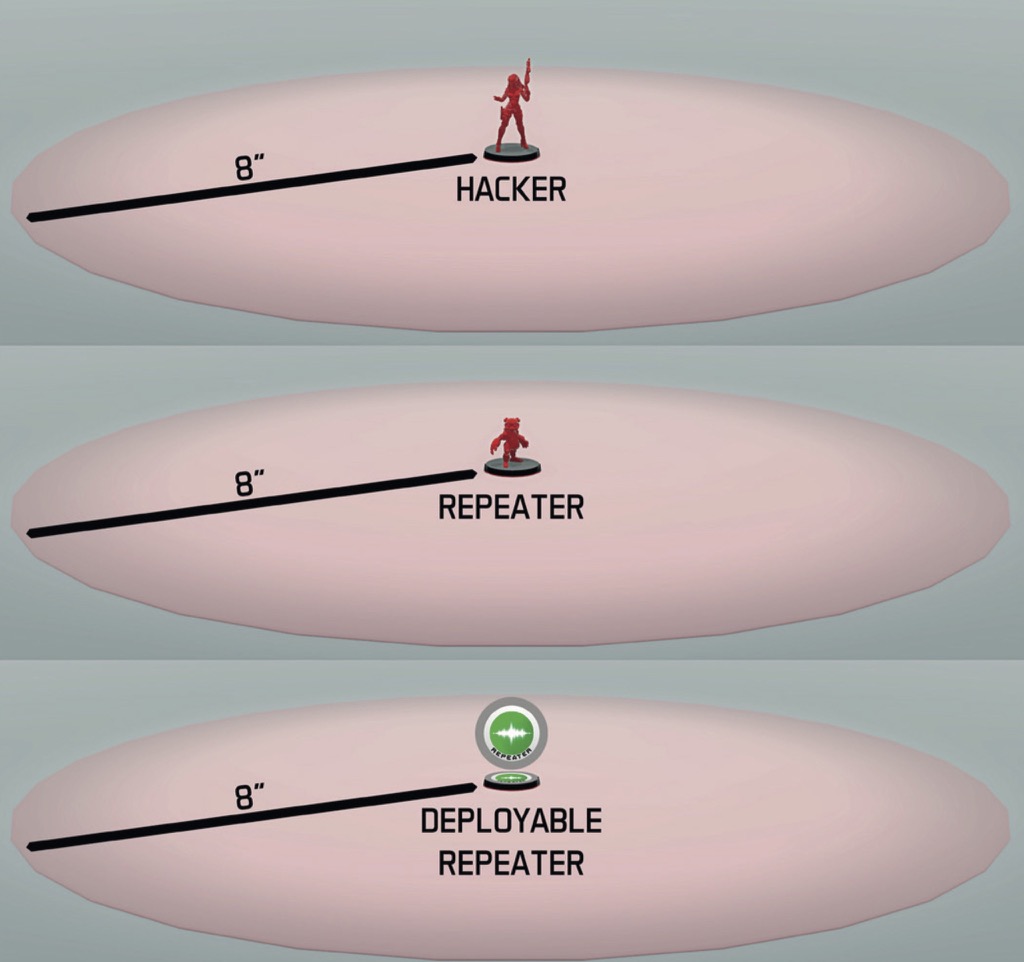
The Hacker may use their Hacking Programs in the area that includes the Zone of Control of the Repeater, the Deployable Repeater and their own Zone of Control.
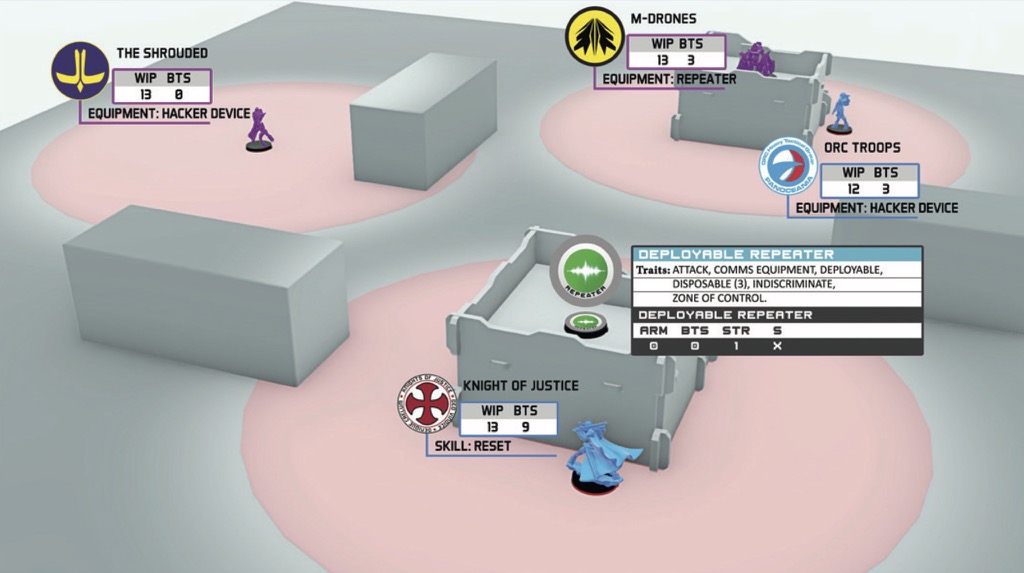
During his Active Turn, the Shrouded Hacker decides to declare Idle as the first Short Skill of the Order. As shown in the picture, he is outside his enemies LoF, but since he is a Hacker, he can use the Deployable Repeater, and the M-Drone Trooper (who carries the Repeater piece of Equipment), to increase his Hacking Area, allowing him to act from his current position.
Therefore, since both the Knight of Justice and the Orc Trooper Hacker are clearly within the Hacking Area of the Shrouded Hacker, they each declare their AROs.
The Knight of Justice declares Reset as their ARO and the Orc Hacker declares Oblivion.
The second Skill of the Shrouded Hacker is Carbonite, dividing his B2 between the Knight of Justice and the Orc Hacker.
During the Resolution of the Order, it is verified that both the Knight of Justice and the Orc Hacker are within the Hacking Area of the Shrouded Hacker.
The following Face to Face Rolls occur:
- Reset by the Knight of Justice vs Carbonite from the Shrouded.
- No Modifiers (MOD).
- Oblivion from the Orc Hacker vs Carbonite from the Shrouded.
- Orc Hacker MODs:
- -3 Firewall MOD for using an Enemy Repeater.
- Shrouded MODs:
- If a Saving Roll is required, the Attack Damage of Oblivion will suffer a -3 MOD from the Firewall.
- Orc Hacker MODs:
FAQs & Errata
Q: How do Hacking Area AROs work, and do they allow the Trooper to Dodge?
A: Hacking Program AROs and Reset AROs are considered valid AROs for a Hacker if the Active Trooper is inside the Hacker’s Hacking Area. Dodge AROs are not considered valid for Hacking Area AROs.
Related Pages: Dodge, Hacking Area, Reset
[Errata] In the Hacking example (p61), the Knight of Justice and the Orc both declare an ARO but this appears to contradict the rules for AROs.
Remember that non-LoF AROs can be declared anyway, and then in the ARO Check step you find out if the ARO was valid.
Related Pages: Hacking Area, Reset
Hacker | Firewall | Hacking Area | Repeater | Deployable Repeater | Hacking Programs Chart | Hacking Device
Programs and StatesAssisted Fire | Carbonite & Immobilized-B State | Controlled Jump | Cybermask & Impersonation State | Enhanced Reaction | Fairy Dust | Oblivion & Isolated State | Spotlight & Targeted State | Total Control & Possessed State | Trinity | White Noise | Zero Pain