NOTICE: Infinity N5.2 and N5 FAQ 0.0.0
The wiki has been updated to include the N5.2 changes and the v0.0.0 FAQ.
List of wiki pages updated in N5.2.
Difference between revisions of "Hacking Area"
m |
(See Also HoloMask State and Hacker/Hackable status, Cautious Movement, fixed HoloMask links.) |
||
| (One intermediate revision by the same user not shown) | |||
| Line 13: | Line 13: | ||
| − | ==[[HoloMask]] and Hacking Area== | + | ==[[HoloMask State | HoloMask]] and Hacking Area== |
When using an [[Enemy]] [[Repeater]] to include an Enemy Trooper in the Hacking Area, any [[ARO]] or [[Hacking Program]] against a Trooper who does not have the [[Hacker]] Special Skill on their real [[Unit Profile]] will fail its Requirements in the [[Resolution]] step of the Order, and instead an [[Idle]] will be performed. This will reveal that the Enemy Trooper is not a Hacker. | When using an [[Enemy]] [[Repeater]] to include an Enemy Trooper in the Hacking Area, any [[ARO]] or [[Hacking Program]] against a Trooper who does not have the [[Hacker]] Special Skill on their real [[Unit Profile]] will fail its Requirements in the [[Resolution]] step of the Order, and instead an [[Idle]] will be performed. This will reveal that the Enemy Trooper is not a Hacker. | ||
| − | ==[[HoloMask]] and Repeater== | + | ==[[HoloMask State | HoloMask]] and Repeater== |
Similarly, when using an [[Enemy]] Trooper’s [[Repeater]], if that Trooper is in [[HoloMask State]] and does not have a Repeater on their real [[Unit Profile]] then any [[ARO]] or [[Hacking Program]] using their fake Repeater will fail its Requirements in the [[Resolution]] step of the Order, and instead an [[Idle]] will be performed. This will reveal that the Enemy Trooper does not have a Repeater. | Similarly, when using an [[Enemy]] Trooper’s [[Repeater]], if that Trooper is in [[HoloMask State]] and does not have a Repeater on their real [[Unit Profile]] then any [[ARO]] or [[Hacking Program]] using their fake Repeater will fail its Requirements in the [[Resolution]] step of the Order, and instead an [[Idle]] will be performed. This will reveal that the Enemy Trooper does not have a Repeater. | ||
| + | |||
| + | |||
| + | {{see-also-start}} | ||
| + | {{update | PDF 5.2, October 2025}} | ||
| + | '''[[HoloMask State]]''' | ||
| + | * {{erratahighlight}}'''Restriction''': Troopers in HoloMask State cannot replicate the [[Hacker]]/[[Hackable]] status of the imitated Trooper. For example, even if they are imitating a Hacker or a Hackable Trooper, if they enter or are in the enemy's [[Hacking Area]], the player must declare their lack of Hacker/Hackable status. | ||
| + | {{erratahighlight-end}} | ||
| + | {{update-end}} | ||
| + | |||
| + | |||
| + | '''[[Cautious Movement]]''' | ||
| + | * '''Restriction. '''For the Cautious Movement of a '''[[Hackable]] Trooper in [[Model]] form''' to generate no AROs, it must also begin and end at two points on the game table that lie outside the [[Hacking Area]] of any [[enemy]] [[Hacker]]s. | ||
| + | * If a '''Hackable Trooper is in Model form''' and its Cautious Movement begins or ends inside the Hacking Area of any enemy Hackers, the Trooper generates AROs as usual. <br>If a '''non'''-Hackable Trooper is in Model form and its Cautious Movement begins or ends inside the Hacking Area of any enemy Hackers, this does '''not''' cause the Trooper to generate AROs. | ||
| + | {{see-also-end}} | ||
| Line 30: | Line 44: | ||
{{greybox-start | Example of Hacking Area and AROs Through Repeaters }} | {{greybox-start | Example of Hacking Area and AROs Through Repeaters }} | ||
| − | |||
| − | |||
| − | |||
| − | |||
{{image | name=n5/eng-hacking-area-example-aros.jpg | style=fullborder }} | {{image | name=n5/eng-hacking-area-example-aros.jpg | style=fullborder }} | ||
| Line 40: | Line 50: | ||
During his Active Turn, a Hacker decides to declare Idle as the first Basic Short Skill of the Order. As shown in the picture, he is outside his enemies' LoF and ZoC, but since he is a Hacker, he can use the Deployable Repeater and a Trooper with the Repeater piece of Equipment to increase his Hacking Area, allowing him to act from his current position. | During his Active Turn, a Hacker decides to declare Idle as the first Basic Short Skill of the Order. As shown in the picture, he is outside his enemies' LoF and ZoC, but since he is a Hacker, he can use the Deployable Repeater and a Trooper with the Repeater piece of Equipment to increase his Hacking Area, allowing him to act from his current position. | ||
| − | Therefore, since the Hacker is within the Hacking Area of the Enemy Hacker, | + | {{update | PDF 5.2, October 2025}} |
| + | Therefore, since the {{erratahighlight}}Active{{erratahighlight-end}} Hacker is within the Hacking Area of the Enemy Hacker, {{erratahighlight}}this one{{erratahighlight-end}} declares his ARO: Oblivion. | ||
| − | As the Enemy Heavy Infantry is in the Active Trooper's Hacking Area, they can declare an ARO, choosing to declare a Reset. | + | {{erratahighlight}}The Enemy Heavy Infantry (HI) cannot declare an ARO as the Active Hacker is outside their LoF and ZoC.{{erratahighlight-end}} |
| + | |||
| + | The second Skill of the {{erratahighlight}}Active{{erratahighlight-end}} Hacker is Carbonite, dividing his B2 between the Enemy Heavy Infantry and the enemy Hacker. | ||
| + | |||
| + | {{erratahighlight}}As the Enemy Heavy Infantry has been targeted by a Hacking Program (a Comms Attack), they can declare an ARO, choosing to declare a Reset.{{erratahighlight-end}} | ||
| + | {{update-end}} | ||
| + | {{original}} | ||
| + | Therefore, since the Hacker is within the Hacking Area of the Enemy Hacker, {{originalhighlight}}the enemy{{originalhighlight-end}} declares his ARO: Oblivion. | ||
| + | |||
| + | {{originalhighlight}}As the Enemy Heavy Infantry is in the Active Trooper's Hacking Area, they can declare an ARO, choosing to declare a Reset.{{originalhighlight-end}} | ||
The second Skill of the Hacker is Carbonite, dividing his B2 between the Enemy Heavy Infantry and the enemy Hacker. | The second Skill of the Hacker is Carbonite, dividing his B2 between the Enemy Heavy Infantry and the enemy Hacker. | ||
| + | {{original-end}} | ||
The following Face to Face Rolls occur: | The following Face to Face Rolls occur: | ||
| Line 79: | Line 100: | ||
[[Category: Hacking]] | [[Category: Hacking]] | ||
| + | |||
| + | [[Category: N5.2 Update]] | ||
Latest revision as of 11:23, 31 October 2025
Hacker | Firewall | Hacking Area | Repeater | Deployable Repeater | Hacking Programs Chart | Hacking Device
Hacking ProgramsAssisted Fire | Carbonite | Controlled Jump | Cybermask | Enhanced Reaction | Fairy Dust | Oblivion | Spotlight | Total Control | Trinity | White Noise | Zero Pain
This term refers to the Area of Effect of Hacking Programs. In Infinity a Hacker’s Hacking Area matches their Zone of Control, and the Zone of Control of Repeaters and Deployable Repeaters of either the Player or their Allies.
In addition, if a Hacker is within the Zone of Control of an Enemy Repeater or Deployable Repeater, their Hacking Area includes all Enemy Troopers on the game table. However, if the Enemy Trooper is not a Hacker, any ARO or Hacking Program using the Enemy Repeater will fail its Requirements, and instead an Idle will be performed.
Hacking Area in ARO
Enemies entering or acting inside the Hacking Area of a Hacker while remaining outside that Hacker’s LoF and ZoC can be reacted to.
In the ARO Check steps of the Order Expenditure Sequence, players can check if the Active Trooper is inside any Reactive Troopers’ Hacking Areas. Measurements must always be made from the Active Trooper, checking a maximum of 8 inches from any point along their path, and from the Active Trooper’s Repeaters. If the measurements show that the Active Trooper is within the Hacking Area of the Reactive Trooper, they can declare an ARO.
HoloMask and Hacking Area
When using an Enemy Repeater to include an Enemy Trooper in the Hacking Area, any ARO or Hacking Program against a Trooper who does not have the Hacker Special Skill on their real Unit Profile will fail its Requirements in the Resolution step of the Order, and instead an Idle will be performed. This will reveal that the Enemy Trooper is not a Hacker.
HoloMask and Repeater
Similarly, when using an Enemy Trooper’s Repeater, if that Trooper is in HoloMask State and does not have a Repeater on their real Unit Profile then any ARO or Hacking Program using their fake Repeater will fail its Requirements in the Resolution step of the Order, and instead an Idle will be performed. This will reveal that the Enemy Trooper does not have a Repeater.
Update PDF 5.2, October 2025
HoloMask State
- Restriction: Troopers in HoloMask State cannot replicate the Hacker/Hackable status of the imitated Trooper. For example, even if they are imitating a Hacker or a Hackable Trooper, if they enter or are in the enemy's Hacking Area, the player must declare their lack of Hacker/Hackable status.
- Restriction. For the Cautious Movement of a Hackable Trooper in Model form to generate no AROs, it must also begin and end at two points on the game table that lie outside the Hacking Area of any enemy Hackers.
- If a Hackable Trooper is in Model form and its Cautious Movement begins or ends inside the Hacking Area of any enemy Hackers, the Trooper generates AROs as usual.
If a non-Hackable Trooper is in Model form and its Cautious Movement begins or ends inside the Hacking Area of any enemy Hackers, this does not cause the Trooper to generate AROs.
Examples

The Hacker may use their Hacking Programs in the area that includes the Zone of Control of the Repeater, the Deployable Repeater and their own Zone of Control.
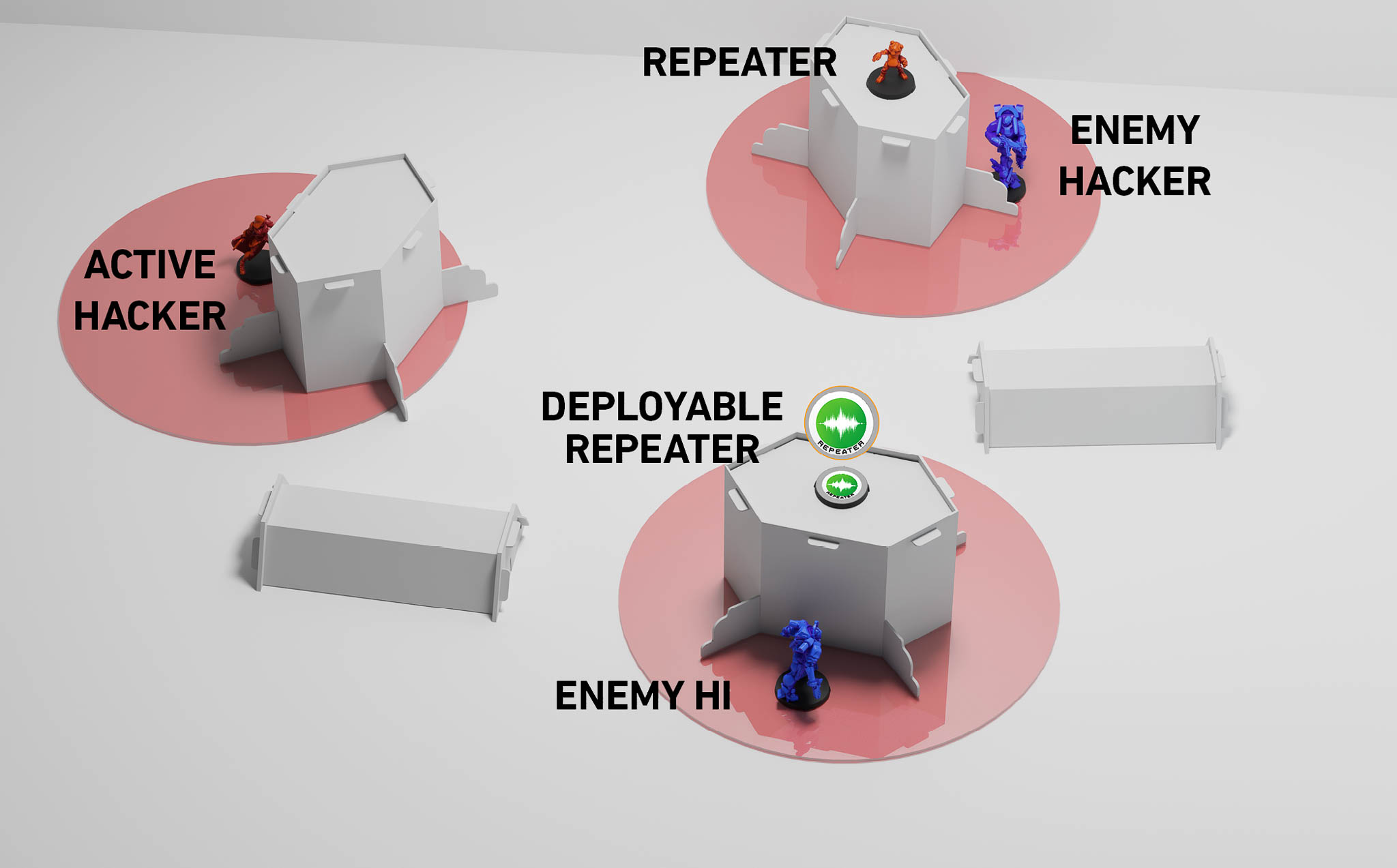
For the sake of simplicity, in this example, the Stealth Special Skill is not being used.
During his Active Turn, a Hacker decides to declare Idle as the first Basic Short Skill of the Order. As shown in the picture, he is outside his enemies' LoF and ZoC, but since he is a Hacker, he can use the Deployable Repeater and a Trooper with the Repeater piece of Equipment to increase his Hacking Area, allowing him to act from his current position.
Update PDF 5.2, October 2025
Therefore, since the Active Hacker is within the Hacking Area of the Enemy Hacker, this one declares his ARO: Oblivion.
The Enemy Heavy Infantry (HI) cannot declare an ARO as the Active Hacker is outside their LoF and ZoC.
The second Skill of the Active Hacker is Carbonite, dividing his B2 between the Enemy Heavy Infantry and the enemy Hacker.
As the Enemy Heavy Infantry has been targeted by a Hacking Program (a Comms Attack), they can declare an ARO, choosing to declare a Reset.
Show original text.
Original
Therefore, since the Hacker is within the Hacking Area of the Enemy Hacker, the enemy declares his ARO: Oblivion.
As the Enemy Heavy Infantry is in the Active Trooper's Hacking Area, they can declare an ARO, choosing to declare a Reset.
The second Skill of the Hacker is Carbonite, dividing his B2 between the Enemy Heavy Infantry and the enemy Hacker.
The following Face to Face Rolls occur:
Reset by the Enemy Heavy Infantry vs Carbonite from the Hacker.
- No Modifiers (MOD).
Oblivion from the Enemy Hacker vs Carbonite from the Hacker.
- Enemy Hacker MODs:
- -3 Firewall MOD for using an Enemy Repeater.
- Hacker MODs:
- No Modifiers (MOD).
If a Saving Roll is required, the Possibility of Survival (PS) of Oblivion will suffer a +3 MOD from the Firewall.
This time, the Hacker is in Camouflaged State and declares Idle.
As the Camouflaged Marker is inside the Enemy Hacker's Hacking Area, the Enemy Hacker can delay their ARO in case the Camouflaged Marker is a Hacker.
The Enemy Hacker may declare an ARO only if the Camouflaged Marker reveals themselves with the second Short Skill of the Order.
Hacker | Firewall | Hacking Area | Repeater | Deployable Repeater | Hacking Programs Chart | Hacking Device
Hacking ProgramsAssisted Fire | Carbonite | Controlled Jump | Cybermask | Enhanced Reaction | Fairy Dust | Oblivion | Spotlight | Total Control | Trinity | White Noise | Zero Pain