NOTICE: Infinity N5.2 and N5 FAQ 0.0.0
The wiki has been updated to include the N5.2 changes and the v0.0.0 FAQ.
List of wiki pages updated in N5.2.
Difference between revisions of "Quantronic Combat (Hacking)"
| Line 72: | Line 72: | ||
Facing the possibility that the Jujak had passed within the Hacker’s ZoC, the Active Player declares Reset. They do not declare BS Attack to face the Hacker because it is clear that during their entire path they lack LoF to the Shrouded Hacker. | Facing the possibility that the Jujak had passed within the Hacker’s ZoC, the Active Player declares Reset. They do not declare BS Attack to face the Hacker because it is clear that during their entire path they lack LoF to the Shrouded Hacker. | ||
| − | + | {{image | name=eng-hacking-example-1.jpg | style=512border }} | |
| Line 86: | Line 86: | ||
They both succeed, but the 7 cancels the 3. | They both succeed, but the 7 cancels the 3. | ||
| − | + | {{image | name=eng-hacking-example-2.jpg | style=512border }} | |
| Line 97: | Line 97: | ||
Due to the 6, the Jujak places an Immobilized-B Token next to him. | Due to the 6, the Jujak places an Immobilized-B Token next to him. | ||
| − | + | {{image | name=eng-hacking-example-3.jpg | style=512border }} | |
{{greybox-end}} | {{greybox-end}} | ||
Revision as of 11:18, 29 April 2020
Combat Module Intro || Damage | Saving Rolls | Wounds and Structure | Unconscious | Dead | Guts Rolls || Ballistic Skills | BS Attack | Template Weapons and Equipment | Direct Template Weapons | Impact Template Weapons | Ranged Weapon Profile | Speculative Attack | Intuitive Attack || Close Combat | CC Attack | Engaged State | Melee Weapon Profile || Quantronic Combat (Hacking)
In Infinity CodeOne, infowar and cyberwarfare tasks, defined as Hacking, falls upon the Hackers’ shoulders, those Troopers equipped with Hacking Devices.
Getting Started with Hacking
According to their nature, Hacking Programs allow the Hacker to act in an aggressive or defensive manner, support other Troopers, interact with scenery, etc.
When making your Army Lists in Infinity Army, a summary of the Hacking Programs will be included, in the same way that a summary of your Troopers’ weapons is included.
Hacking Devices and Hacking Programs: Characteristics
Hacking Devices and Hacking Programs have the following characteristics:
- They act in the user's Hacking Area.
- They do not require LoF to act, unless the Hacking Program's own description states otherwise.
They benefit, if applicable, from the target's Targeted State.
Hacking Area
This term refers to the Area of Effect of Hacking Programs. In Infinity CodeOne a Hacker's Hacking Area matches their Zone of Control.
Key to the Hacking Programs Quick Reference Chart
Each Hacking Program grants a series of MODs and advantages when used, that are reflected in charts listing following information:
- Attack MOD. A MOD that is applied to the user's WIP Attribute.
- Opponent's MOD. A MOD that is applied to an enemy Trooper's Attribute when performing a Face to Face Roll.
- Damage. The value used to determine the Damage when applying a successful Hacking Program Roll. Unless otherwise stated, the Attribute used in the Saving Roll to resist Damage from a Hacking Program is BTS.
- Burst. The number of dice the Active Player must roll when declaring the Hacking Program. When the B value is higher than 1, it may be concentrated on a single target or be divided among several targets.
- Remember that in the Reactive Turn the B value is generally 1, unless modified by a rule or Skill.
- Target. The Troop Type that can be targeted by the Hacking Program.
- Type of Skill. Indicates the type of Skill (Entire Order, Short Skill, ARO, etc.) that must be spent to use the Hacking Program.
- Special. Indicates the special effects that the Hacking Program's user may apply. This section may also indicate a State that will be imposed on the target, or the type of Ammunition and Traits that may apply.
Unless otherwise stated, the range of every Program is always the Hacker's Hacking Area.
Hacking Programs Chart
| Name | Attack MOD | Opp. MOD | DAM | B | Target | Skill Type | Special |
|---|---|---|---|---|---|---|---|
| Carbonite | 0 | 0 | 13 | 2 | TAG, HI, REM, Hacker | Short Skill/ARO | DA Ammo, Non-Lethal, State: Immobilized-B. |
| Spotlight | 0 | 0 | -- | 1 | -- | Short Skill/ARO | Non-Lethal, State: Targeted. |
Hacking Devices
| Device | Program 1 | Program 2 |
|---|---|---|
| Hacking Device | Carbonite | Spotlight |
Example of Quantronic Combat (Hacking)
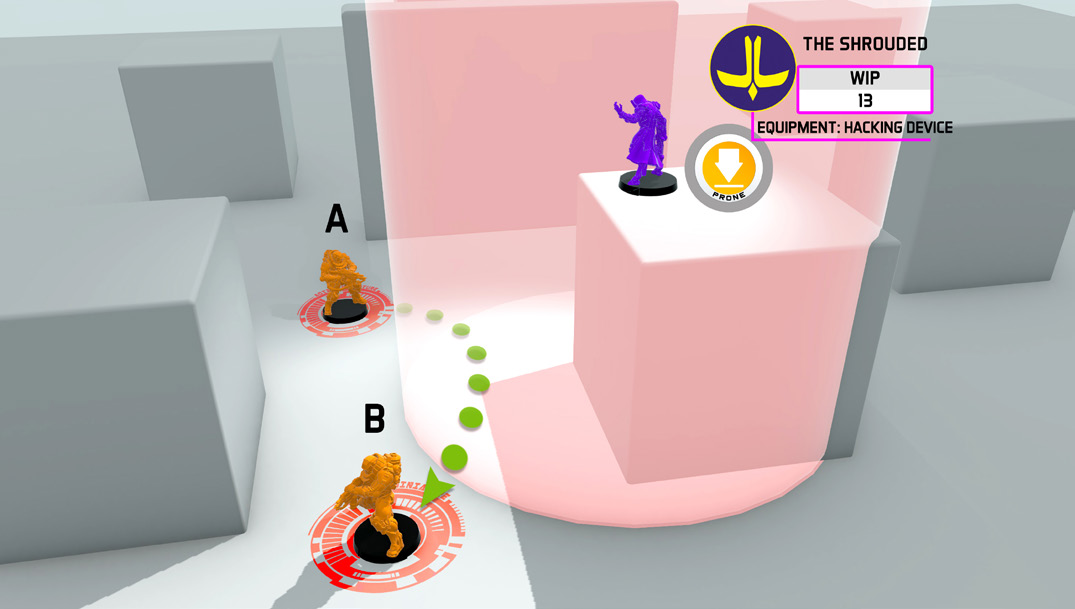
Step 1:
The Active Player declares Move with their Jujak from point A to B.
The Reactive Player declares the use of the Carbonite Hacking Program with their Shrouded Hacker.
Facing the possibility that the Jujak had passed within the Hacker’s ZoC, the Active Player declares Reset. They do not declare BS Attack to face the Hacker because it is clear that during their entire path they lack LoF to the Shrouded Hacker.
Step 2:
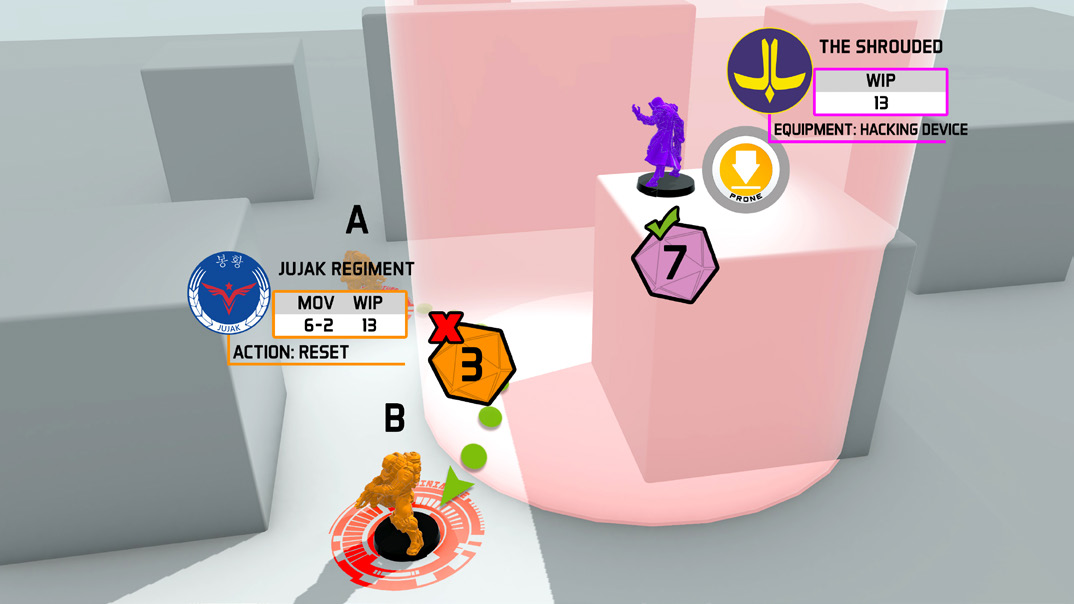
It is found that, during their Movement, the Jujak indeed entered the Hacker’s ZoC and the Face to Face Rolls are performed.
Face to Face Roll:
Active Player, Reset (WIP Roll, in this case there are no MODs to be applied): 1 d20 with Success Value (SV) = 13.
Reactive Player, Carbonite (WIP Roll, in this case there are no MODs to be applied): 1 d20 with SV = 13.
They both succeed, but the 7 cancels the 3.
Step 3:
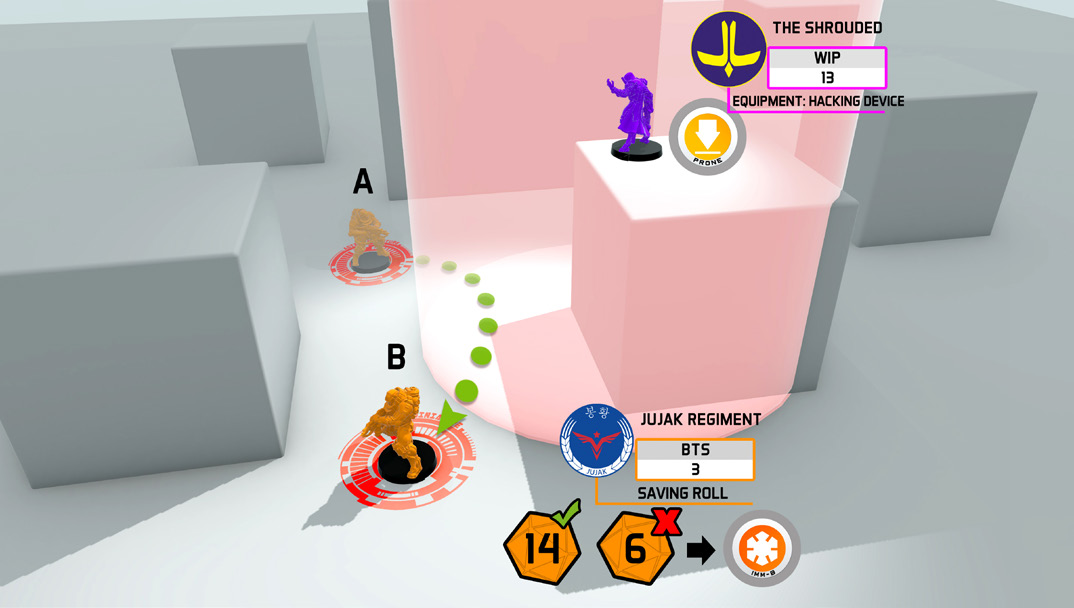
Therefore, after the Shrouded Hacker won the Face to Face Roll, the Jujak must perform 2 Saving Rolls due to the DA Ammunition’s against Damage 13.
Attack Damage = 10 (13 - 3 due to BTS).
Due to the 6, the Jujak places an Immobilized-B Token next to him.
Combat Module Intro || Damage | Saving Rolls | Wounds and Structure | Unconscious | Dead | Guts Rolls || Ballistic Skills | BS Attack | Template Weapons and Equipment | Direct Template Weapons | Impact Template Weapons | Ranged Weapon Profile | Speculative Attack | Intuitive Attack || Close Combat | CC Attack | Engaged State | Melee Weapon Profile || Quantronic Combat (Hacking)